External Attack Surface Assessment
Contact Us
Is your organization prepared to face evolving cyber threats head-on?
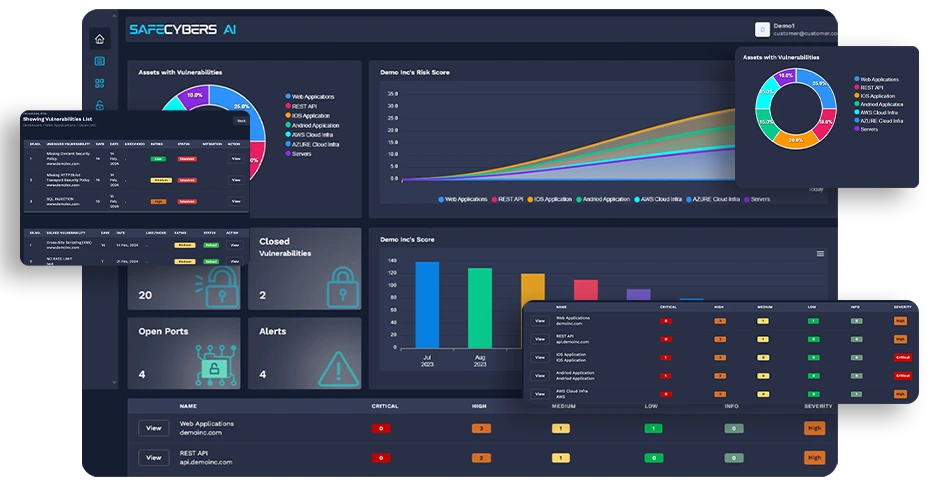
SAFE CYBERS AI a single platform that discovers, evaluates, and responds to vulnerabilities throughout an external attack surface while calculating a risk score. The SAFE CYBERS AI platform continuously scans and detects asset threats, vulnerabilities, and risks. Also, SAFE CYBERS AI platform does the intel analysis to prioritize exploitable risks.
SAFE CYBERS AI always on pentesting that combines manual and automated testing with 24/7 scanning, consultation and streamlined communication and reporting delivered through a single AI platform. By delivering pentesting “as a service,” organizations receive a broader, more thorough vulnerability audit year-round instead of relying on one-time pentest.
Discover in-depth information about the attack surface and asset base of Enterprise, as well as potential entry points and weaknesses that hackers may exploit.
SAFE CYBERS Cyber Threat Intelligence and real-world exploit data. This model produces a probability score. The likelihood that a vulnerability will be exploited increases with score.
With the SAFECYBERS Cyber Risk Score driven by AI, you may acquire a clear understanding of the risk assessment of your apps and receive a thorough explanation of an organization's security posture.
Safeguard applications, company data from internal, external and malicious attacks. Ensures complete risk management and safeguards against external data threats.
When it comes to hacking, cybercriminals don't adhere to any rules, they'll enter by whatever means required. Hacker View protects your data by offering an inside look at potential exploits and insight into how hackers work. Get a unique glimpse into your assets vulnerabilities from the eyes of a hacker. Identify potential security threats before they can be exploited.
What Are The Benefits Of Vulnerability Assessment & Penetration Testing (VAPT)?
-
Presents a detailed view of potential threats existing within a system or application
-
Spots programming errors which make the application prone to cyber attacks
-
Ensures complete risk management and safeguards against external data threats
-
Secures business from scenarios wherein reputation and money are at stake
-
Safeguard applications, company data from internal, external and malicious attacks
Our Assessment Methodology




Strengthen your security with our comprehensive pentest platform





Cloud infrastructure VAPT is important because cloud environments can be complex and dynamic, with multiple layers of infrastructure and services that may be managed by different providers. This complexity can make it challenging to identify and address vulnerabilities. Additionally, cloud infrastructure is often targeted by attackers due to the sensitive data and resources that are often stored in the cloud.
SAFECYBERS AI Platform for External Cybersecurity
Always on Pentesting that combines manual and automated testing with 24/7 scanning, consultation and streamlined communication and reporting delivered through a single platform. By delivering pentesting “as a service,” organizations receive a broader, more thorough vulnerability audit year-round instead of relying on one-time pentests, which are typically executed just once a year.
To ensure critical assets are secure and their entire attack surface has some level of pentesting coverage, today's modern enterprise requires a more continuous and comprehensive penetration testing process.
One time penetration testing has its limitations. Once a test has been completed, how can one be sure that no new vulnerabilities arise during the remaining 364 days of the year?
24 x 7 x 365 continues view
The Risk Profile displays the overall Cyber Risk Score of your application, representing the cyber risk health based on your external attack surface. This score is calculated based on categories of issues detected, which are grouped and weighted based on their impact, severity, and risk.
-
Full cyber security risk scorecard
-
Up-to-date visibility of vulnerabilities
Frequently Asked Questions
Vulnerability assessment is a process of identifying, evaluating, and prioritizing vulnerabilities in a system, cloud-Infra, network, or application. It involves reviewing and analyzing potential security weaknesses that could be exploited by attackers to gain unauthorized access or compromise the confidentiality, integrity, or availability of the system.
The goal of vulnerability assessment is to identify vulnerabilities before they are exploited by attackers and to take appropriate measures to mitigate or eliminate the risk. This can include identifying configuration errors, software flaws, weak passwords, and other vulnerabilities that could be exploited by attackers.
Penetration testing also known as pen testing, is an in-depth expert-driven activity focused on identifying various possible routes an attacker could use to break into the network. In-addition with the vulnerabilities it also identifies the potential damage and further internal compromise an attacker could carry out once they are past the perimeter. The goal of the test is to identify and document any vulnerabilities that could be exploited by attackers, as well as to provide recommendations for improving the security of the system. The results of the test are typically provided to the organization in a detailed report, which includes recommendations for improving the security of the system.
Vulnerability Assessment and Penetration Testing are both critical components of a comprehensive security program. Here are some of the reasons why they are needed:
- Identify and Prioritize Risks: VA and Pen Testing help organizations identify and prioritize potential risks and vulnerabilities in their IT systems, networks, and applications. By performing regular assessments and testing, an organization can gain a better understanding of its security posture and prioritize efforts to mitigate the most critical vulnerabilities.
- Comply with Regulations: Many industry regulations and standards, such as PCI-DSS, HIPAA, and ISO 27001, require organizations to perform regular VA and Pen Testing to maintain compliance. Failing to comply with these regulations can result in fines, legal penalties, and reputational damage.
- Stay Ahead of Threats: Cyber threats are constantly evolving, and new vulnerabilities are discovered every day. VA and Pen Testing help organizations stay ahead of these threats by identifying vulnerabilities before they can be exploited by attackers.
- Proactive Security: VA and Pen Testing help organizations take a proactive approach to security rather than waiting for a breach to occur. By identifying and addressing vulnerabilities before an attack occurs, an organization can reduce the risk of a successful cyber attack.
- Improve Response Time: In the event of a security incident, having a thorough understanding of an organization’s vulnerabilities can help reduce the time it takes to respond and mitigate the incident.
Overall, VA and Pen Testing are essential components of a comprehensive security program that can help organizations identify and address vulnerabilities, comply with regulations, stay ahead of threats, take a proactive approach to security, and improve incident response times.
If you would like sample VAPT reports, please get in touch with our VAPT experts.
The Vulnerability Assessment and Penetration Testing (VAPT) methodology is a structured approach used to identify and assess vulnerabilities in an organization’s IT systems, networks, and applications.
The VAPT methodology typically involves the following steps:
- Planning and Preparation: This involves defining the scope of the assessment, identifying the systems, networks, and applications to be tested, and obtaining the necessary permissions and approvals.
- Vulnerability Assessment: This involves scanning the systems, networks, and applications for known vulnerabilities using automated tools and manual techniques. The goal is to identify potential weaknesses that could be exploited by attackers.
- Analysis and Reporting: The results of the vulnerability assessment are analyzed and compiled into a detailed report that identifies the vulnerabilities and their severity level. Recommendations for remediation are also included in the report.
- Penetration Testing: Once the vulnerabilities have been identified, the penetration testing phase begins. This involves attempting to exploit the identified vulnerabilities in a controlled environment to determine the impact and severity of a potential attack.
- Reporting and Remediation: The results of the penetration testing are analyzed and compiled into a detailed report that includes the steps required to remediate the vulnerabilities. The report is presented to the organization’s management, and remediation efforts are initiated.
- Validation and Follow-up: After the remediation efforts are complete, the VAPT team performs a follow-up assessment to ensure that the vulnerabilities have been properly addressed. This is important to ensure that the organization’s security posture has been improved.
The VAPT methodology is a continuous process that involves regular assessments and testing to ensure that an organization’s IT systems, networks, and applications remain secure over time. By following this methodology, organizations can identify and address vulnerabilities before they can be exploited by attackers and maintain a strong security posture.
VAPT is similar to software patching: One of the biggest misconceptions that people have is that VAPT performs a similar function as software patching. When in actual software patching is a part of vulnerability management that mitigates risks and threats in the system but goes way beyond this. It reaches other endpoints where vulnerabilities require fixes. It can be system configuration settings, firewall policies, registry keys, open ports, etc.
Only serious vulnerabilities must be fixed: There can be cases when the system is exposed to multiple breaches and errors. Often companies keep their focus on remediating critical vulnerabilities which are singled out based on CVSS scores. However, this is not an effective or surest way of handling a vulnerability management program. So if you detect a low-level vulnerability, it should not be ignored because it might impact multiple endpoints and therefore applies more risk than a critical vulnerability present which can be presented at 1 or 2 endpoints. To assess the criticality of a vulnerability, the endpoints it affects are important to be gauged. One must assess critical factors that include its sphere of impact, its age, current exploit activity, etc.
“VAPT is a one-time exercise”: Many organizations believe that VAPT is a one-time exercise and that once vulnerabilities are identified and remediated, they no longer need to be concerned about security. However, VAPT should be performed regularly, as new vulnerabilities are constantly being discovered, and the threat landscape is continually evolving.
“VAPT is only for large organizations”: Smaller organizations often believe that VAPT is only necessary for large organizations with complex IT systems. However, all organizations, regardless of size, are vulnerable to cyber attacks and should perform VAPT regularly to identify and address vulnerabilities.
“Automated tools can replace VAPT”: While automated tools can be helpful in identifying known vulnerabilities, they cannot replace the expertise of a trained VAPT professional. Penetration testing, in particular, requires manual testing and analysis to identify vulnerabilities that automated tools may miss.
“VAPT is only for compliance”: Many organizations believe that VAPT is only necessary to comply with industry regulations and standards. However, VAPT is an essential component of a comprehensive security program and should be performed regardless of compliance requirements.
Overall, VAPT is a critical component of a comprehensive security program, and it is essential to understand the realities of VAPT and not be misled by myths and misconceptions.
A major threat faced by organization systems is a data breach which can result in financial losses, reputational damage, and other negative consequences as a result of their sensitive information being compromised. Organizations may face legal and regulatory penalties, loss of customer trust, and other negative consequences.
Here are some ways that VAPT can help defend against data breaches:
- Identify Vulnerabilities: VAPT can help identify vulnerabilities that could be exploited by attackers to gain unauthorized access to an organization’s systems, networks, and applications. By identifying these vulnerabilities, an organization can take steps to remediate them before they can be exploited.
- Test Security Controls: VAPT can test an organization’s security controls, such as firewalls and intrusion detection systems, to ensure they are working as intended. This can help identify gaps or weaknesses in the security controls that could be exploited by attackers.
- Verify Patch Management: VAPT can verify that an organization’s patch management process is working effectively to ensure that software and systems are up to date with the latest security patches. This can help prevent attackers from exploiting known vulnerabilities.
- Test Incident Response: VAPT can test an organization’s incident response plan to ensure that it is effective in responding to a data breach. This can include testing how quickly an organization can detect and respond to a breach, as well as testing the effectiveness of the response plan.
- Raise Awareness: VAPT can help raise awareness among employees about the importance of cybersecurity and the risks of data breaches. This can include training employees on best practices for security, such as strong password management and avoiding phishing emails.
With our integrated portfolio and industry-leading threat intelligence, GS2 gives you the scope, scale, and capabilities to keep up with the complexity and volume of threats.
